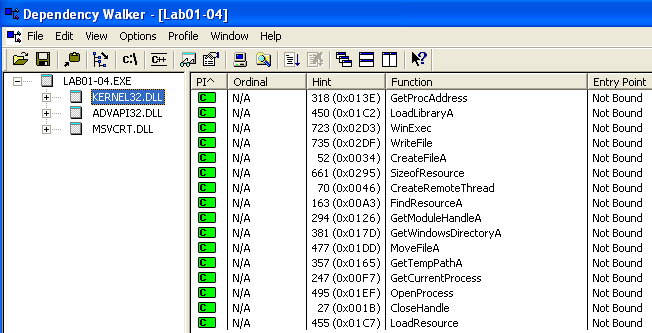
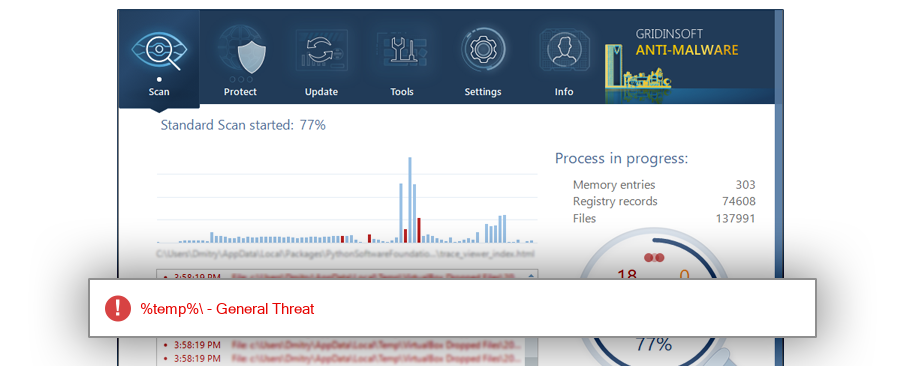
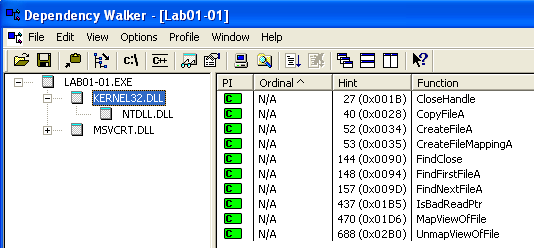
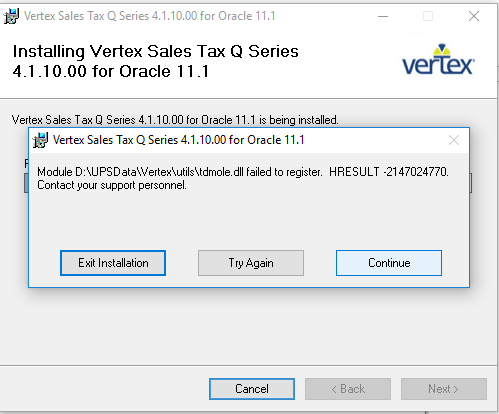
Warning Against Infostealer Infections Upon Executing Legitimate EXE Files ( DLL Hijacking) - ASEC BLOG

Warning Against Infostealer Infections Upon Executing Legitimate EXE Files ( DLL Hijacking) - ASEC BLOG

Warning Against Infostealer Infections Upon Executing Legitimate EXE Files ( DLL Hijacking) - ASEC BLOG

Warning Against Infostealer Infections Upon Executing Legitimate EXE Files ( DLL Hijacking) - ASEC BLOG

Unable to Install malware bytes it is blocked by administrator. - Resolved Malware Removal Logs - Malwarebytes Forums
.png.162a3d14c601ab7ba856a5ad9944b2db.png)